This lab session is a low-level, hands-on introduction to container security using the container tools included with Red Hat Enterprise Linux 8. It is intended to be consumed as a series of self paced exercises.
-
An introductory knowledge of Linux and containers is helpful.
-
Basic text editing skills using
vimornano.
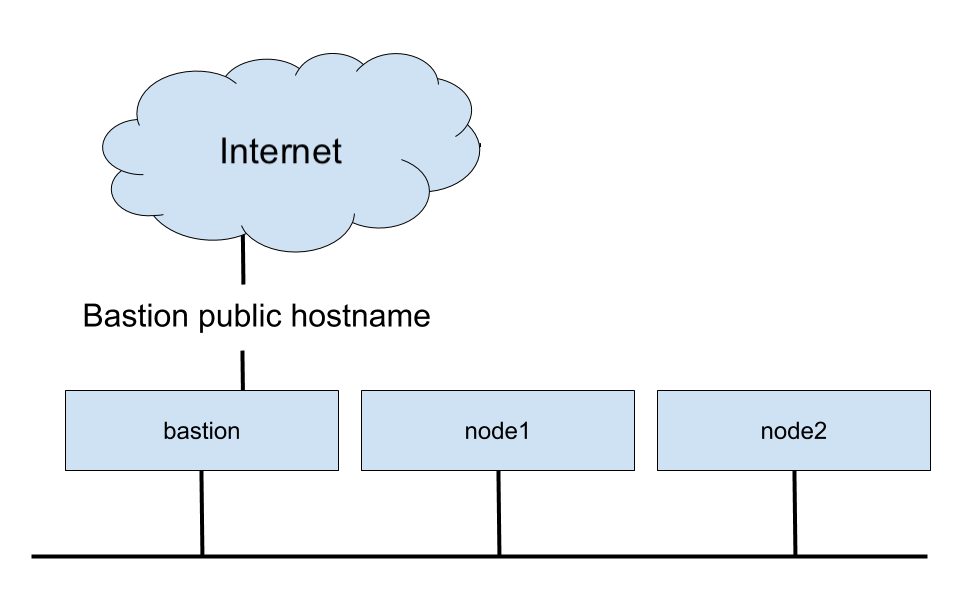
Lab Environment

| Server | Function |
|---|---|
bastion |
External ssh and container host |
node1 |
Image registry and container host |
node2 |
Image registry and container host |
Important
| These servers can not be rebuilt in a timely fashion. |
-
Do not
rmany files or directories you did not create. -
Make a backup copy before modifying any file.
Conventions used in this lab
Shells and Prompts
ec2-user ~ command with sample output.cat /etc/redhat-releaseRed Hat Enterprise Linux release 8.1 (Ootpa)
Getting access to the servers
Use the web console to login to the bastion:
https://bastion-0.example.redhatgov.io:9090/system/terminalUse ssh to login to the nodes, from the bastion:
ssh node1-0.example.redhatgov.io
ssh node2-0.example.redhatgov.ioFor each node, you will be asked to confirm that the key fingerprint is OK, as you haven’t logged into it, before.
Node 1:
The authenticity of host 'node1-0.example.redhatgov.io (10.0.2.128)' can't be established. ECDSA key fingerprint is SHA256:X6KOWD5YgDqcGxnSKDgT0ZYWqBeG8yw9CKTvgFwT6sQ. Are you sure you want to continue connecting (yes/no/[fingerprint])?
Respond with yes or y to accept the key:
yesLogout when done.
Node 2:
The authenticity of host 'node2-0.example.redhatgov.io (10.0.2.125)' can't be established. ECDSA key fingerprint is SHA256:n2/LxFOXS2of8osIEcY/5911N6OmqaJJpsYRgnVrsiA. Are you sure you want to continue connecting (yes/no/[fingerprint])?
Again, respond with yes or y to accept the key:
yesLogout when done.
Now, let’s move on to lab #2!
Workshop Details
| Domain |

|
|
| Workshop | ||
| Student ID |