
Red Hat Container Catalog
While public registries and uncurated repositories are acceptable for some cloud-native development and proof-of-concept projects, they do not always provide content that is fit for production consumption; enterprise workloads require enterprise-ready tools.
MATTHEW HICKSVICE PRESIDENT, ENGINEERING, OPENSHIFT AND MANAGEMENT, RED HAT
While container-based applications have begun moving into production, not all containers are created or maintained equally. Every container starts with a Linux base layer, which means that every ISV building container images is distributing Linux content. For these containers to be used in production environments, this content needs to be free from known vulnerabilities. While other companies, including several Red Hat partners, offer container scanners to help identify security flaws, Red Hat goes further by providing a comprehensive security impact metric, the Container Health Index, as well as access to updated container images addressing known security issues.
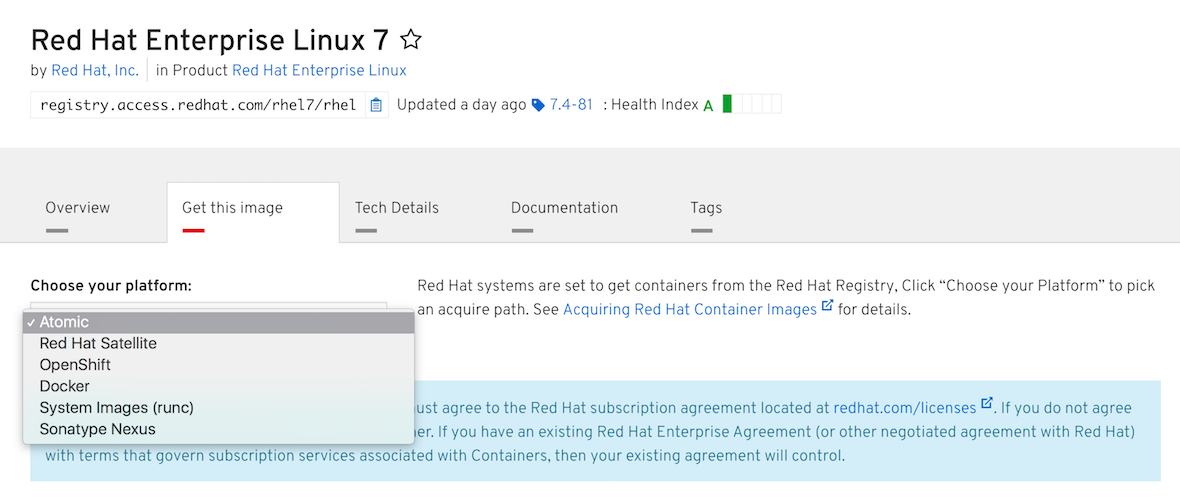
Get This Image
Red Hat systems are set to get containers from the Red Hat Registry, Click “Choose your Platform” to pick an acquire path.
atomic install registry.access.redhat.com/rhel7/rhel# set the organization
ORG="ACME"
# set the product name
PRODUCT="redhat-images"
# create the product
hammer product create --name "${PRODUCT}" \
--description "container images" \
--organization="${ORG}" --organization "${ORG}"oc import-image my-rhel7/rhel --from=registry.access.redhat.com/rhel7/rhel --confirmdocker pull registry.access.redhat.com/rhel7/rhelatomic pull --storage=ostree registry.access.redhat.com/rhel7/rhel
atomic install --system rhel7/rhelImage Metadata
Environment configuration and image metadata information for the RHEL 7 container image found on the Red Hat Container Catalog.
Env
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
container=oci
Cmd
/bin/bash
Labels
com.redhat.component rhel-server-docker
authoritative-source-url registry.access.redhat.com
distribution-scope public
vendor Red Hat, Inc.
description The Red Hat Enterprise Linux Base image is designed to be a fully supported foundation for your containerized applications. This base image provides your operations and application teams with the packages, language runtimes and tools necessary to run, maintain, and troubleshoot all of your applications. This image is maintained by Red Hat and updated regularly. It is designed and engineered to be the base layer for all of your containerized applications, middleware and utilites. When used as the source for all of your containers, only one copy will ever be downloaded and cached in your production environment. Use this image just like you would a regular Red Hat Enterprise Linux distribution. Tools like yum, gzip, and bash are provided by default. For further information on how this image was built look at the /root/anacanda-ks.cfg file.
io.k8s.display-name Red Hat Enterprise Linux 7
summary Provides the latest release of Red Hat Enterprise Linux 7 in a fully featured and supported base image.
vcs-type git
name rhel7
vcs-ref b7f83830183f71d08b6d758479417bb5437877a9
version 7.3
architecture x86_64
release 97
io.openshift.tags base rhel7
build-date 2017-06-21T15:47:06.130692
com.redhat.build-host ip-10-29-120-158.ec2.internalDocumentation
The Container Catalog contains documentation samples on how to get started with the container and any additional relevent documentation for using the container.
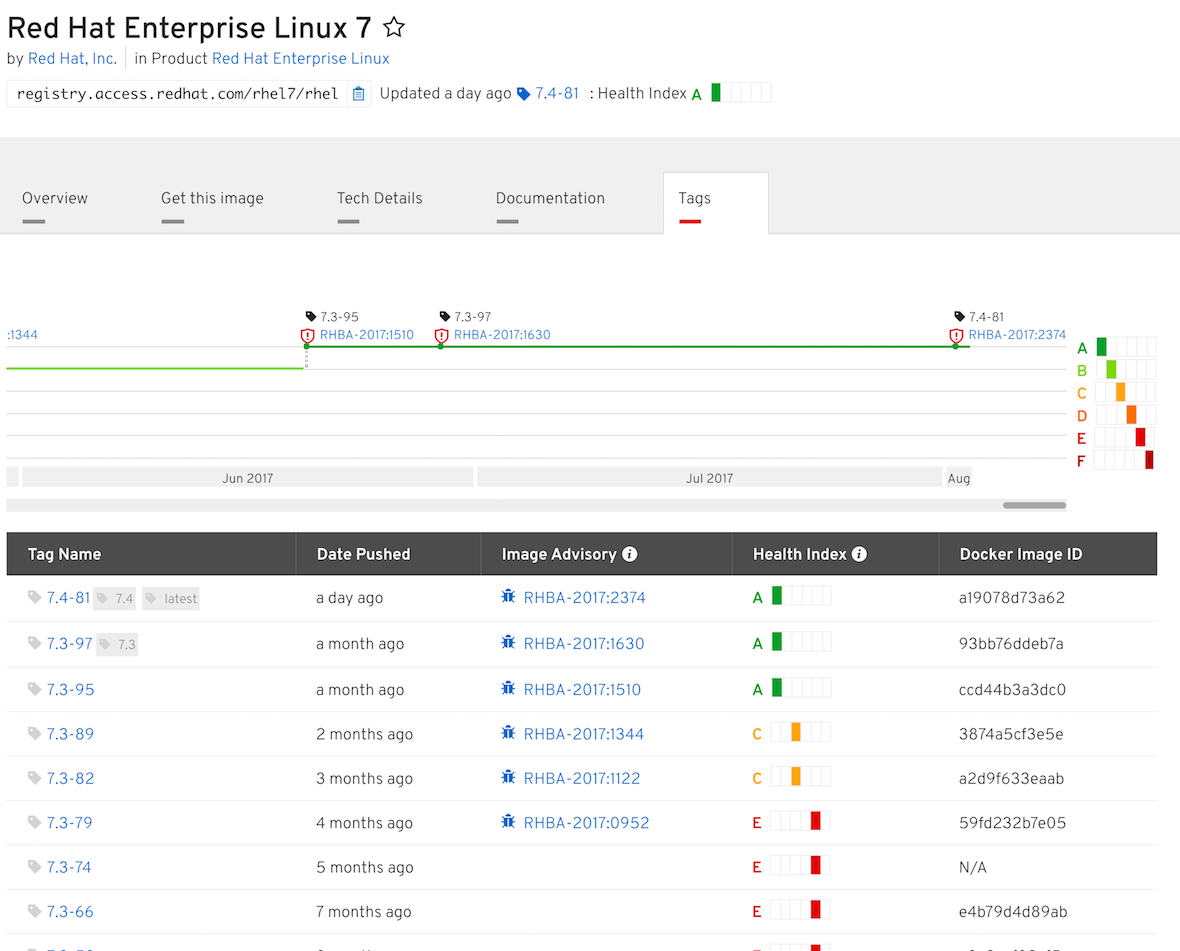
Health
The Container Health Index is an integrated part of the Red Hat Container Catalog, a service for discovering, distributing and consuming commercially-curated Linux container images. Providing a clear delineation between enterprise-class, production-ready containers and their potentially more risk-inducing counterparts, the Red Hat Container Catalog enables customers to easily attain a clear checklist of container contents and other detailed information including:
Container Health Index, a simple system to help enterprise users quickly assess how well-maintained and secure a given image is. Extensive image metadata which goes far beyond image name and description to display the container’s full package list, build environment and complete registry information. Image documentation to help users understand image usage in multiple environments, such as Red Hat OpenShift Container Platform or distribution via Red Hat Satellite. Image advisories for quickly alerting users to any potential issues with a given image or included RPMs.
Red Hat uses the Container Health Index to identify security risk with containers that Red Hat provides through the Red Hat Container Catalog. These containers consume software provided by Red Hat and our errata process, so old, stale container images are much more likely to contain security risks, while new, fresh containers are less likely.
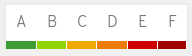
To illustrate this, we use a grading system. The criteria for determining the grade is based on the age and the criticality (rated Critical or Important) of the oldest flaw that is applicable to the container image. Applicable Moderate or Low severity flaws, of any age, do not influence the Container Health Index.
Grade A: This image does not contain known unapplied errata that fix Critical or Important flaws.
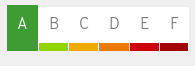
Grade B: This image may be missing Critical or Important security errata, but no missing Critical flaw is older than 7 days and no missing Important flaw is older than 30 days.
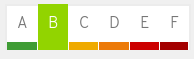
Grade C: This image may be missing Critical or Important security errata, but no missing Critical flaw is older than 30 days and no missing Important flaw is older than 90 days.

Grade D: This image may be missing Critical or Important security errata, but no missing Critical flaw is older than 90 days and no missing Important flaw is older than 365 days.

Grade E: This image may be missing Critical or Important security errata, but no missing Critical or Important flaw is older than 365 days.

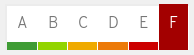
Grade F: This image may be missing Critical or Important security errata, and they are older than 365 days. Or the container is out of its lifecycle.
Grade Unknown: This image cannot be scanned as it is missing metadata required to perform the Container Health Index calculation.